Cybersecurity Month is the ideal time to remind businesses that none are immune to a cyberattack. In 2024, the average ransom demanded by hackers reached 2 million dollars, a 500% increase from the 400,000 dollars demanded in 2023. Additionally, the average cost of system recovery, excluding ransom, rose to 2.73 million dollars, an increase of almost 1 million compared to the previous year. These alarming numbers highlight how crucial it is to be prepared in advance and have well-defined response strategies.
For this reason, the consequences can be disastrous if the correct steps are not taken. In this article, we will explore the measures to be taken after an attack to limit damage, restore systems, and prevent future attacks. Iperius Backup software plays a crucial role in this prevention and recovery strategy, while Iperius Console allows central monitoring of IT systems and remote backup management (centrally check for alerts).
1. Identification and Containment of the Cyberattack
When a cyberattack occurs, the first step is to identify the source and scope of the attack. Whether it’s ransomware, DDoS attacks (Distributed Denial of Service), or data security breaches, it is crucial to contain the incident as quickly as possible to prevent its spread.
Recommended Actions:
- Isolate compromised systems from the network.
- Immediately stop suspicious connections.
Why is Containment Important?
In the digital world, time plays a crucial role during a cyberattack. Every minute of delay can cause significant damage: hackers can access more data, spread malware to other systems, or compromise the entire IT infrastructure. Therefore, immediately containing the attack is crucial to minimize the damage.
Here are some significant statistics:
- 75% of companies affected by ransomware reported that hackers attempted to compromise backups, which makes protecting backups from the start essential through measures such as encryption and data isolation.
- Every minute a system is under attack can result in substantial financial loss, estimated at over $9,000 per minute in sectors such as e-commerce and financial services.
2. Damage Assessment and Data Management
After containing the attack, it is necessary to understand the extent of the damage. Once this is done, the company must focus on restoring systems. Backups are key in this phase. Software like Iperius Backup allows regular backups to be scheduled and quickly restores critical data in the event of an incident.
Recommended Actions:
- Conduct a full audit to identify affected devices and data.
- Update systems to fix identified vulnerabilities.
- Verify system integrity after recovery to avoid any malicious remnants.
- Restore operations using previous Iperius backups.
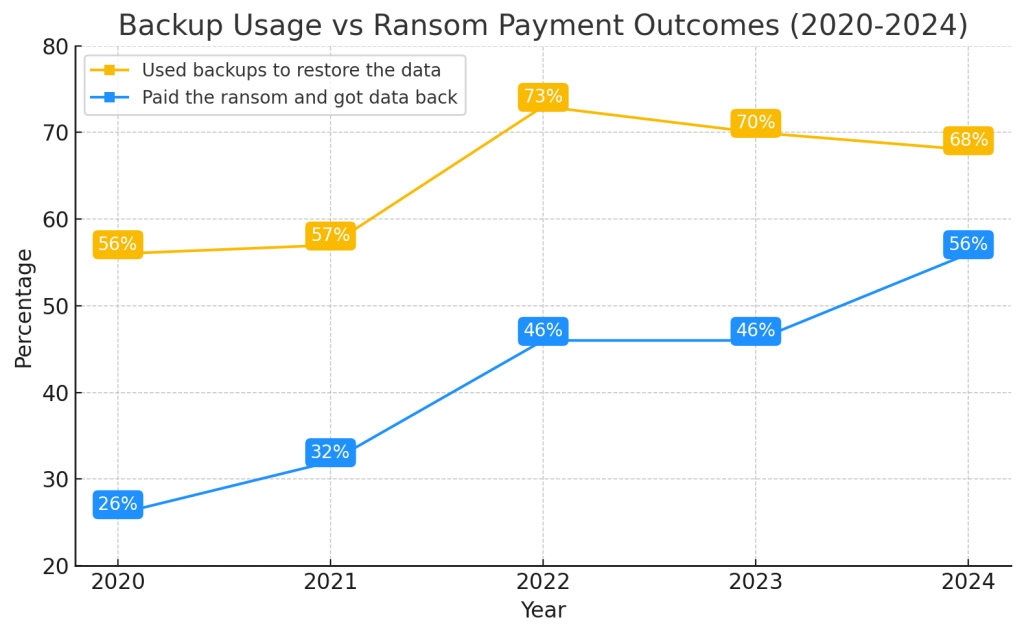
One of the most difficult decisions to face during a ransomware attack is whether to pay the ransom. In reality, it’s not a real choice but a lack of alternatives when a reliable backup system is not available. Paying hackers does not guarantee the complete recovery of data and may encourage future attacks. The following diagram shows the evolution of the use of backups versus ransom payments for data recovery between 2020 and 2024.
As seen in 2024, 56% of affected organizations decided to pay the ransom to recover their data, a significant increase from 26% in 2020. However, using backups to recover data remains one of the best solutions, although it has slightly decreased from 73% in 2022 to 68% in 2024.
Why Not Pay the Ransom?
- Reliability and Security: Restoring data with a secure backup ensures that the company is not dependent on hackers’ demands. Solutions like Iperius Backup offer integrated protection to schedule and monitor regular backups.
- Long-term Savings: Investing in a backup strategy may seem costly initially, but it eliminates the risk of paying ever-higher ransoms.
- Data Integrity: With a backup system like Iperius, you can not only restore data but also constantly monitor the status of your backups with Iperius Console, avoiding the risk of compromise and spread.
Rather than being forced to give in to cybercriminals’ demands, companies should invest in a solid backup strategy that allows for quick and efficient recovery without considering ransom payments.
3. Notification and Communication
If the attack has resulted in a breach of personal or sensitive data, it is essential to comply with legal obligations, such as notifying regulators and stakeholders. In some cases, penalties may be imposed if the attack is not reported within the required timeframe. Transparent communication with employees, partners, and customers is essential to maintain trust.
Recommended Actions:
- Notify the competent authorities in case of personal data leaks (as required by GDPR in Europe).
- Train employees on the measures to be taken and the security guidelines to follow.
- Prepare public statements for the media, in case the attack becomes public.
4. Post-Incident Analysis and Security Enhancement
After restoring systems following a cyberattack, it is essential to reflect on the incident to strengthen corporate defenses and prevent future attacks. This phase requires a thorough review of security policies, as in 32% of ransomware attacks, unpatched vulnerabilities were exploited. Network scans can help identify and fix these weak points.
Strengthening firewalls and implementing multi-factor authentication (MFA) are essential steps to protect access, especially considering that 29% of attacks were due to compromised credentials. Additionally, using tools like Iperius Console for constant real-time activity monitoring allows for the identification of anomalies and reduces the risk of future attacks. Keep in mind that in 94% of ransomware attacks, criminals attempted to compromise backups as well.
Finally, it is crucial to invest in staff training, as advanced technologies cannot replace a well-informed team. Creating a security culture within the organization, where all employees are aware of the risks and best practices, is essential to ensure lasting protection.
Conclusion
Reacting quickly after an attack is crucial to safeguarding the company. Investing in solutions like Iperius Backup and Iperius Console helps protect data and create a safer environment.
Every minute counts during an attack; planning and constant monitoring can significantly reduce risks. Review your security policies, update your systems, and prepare your team. Your company deserves to be protected from future attacks, and security starts now.


PLEASE NOTE: if you need technical support or have any sales or technical question, don't use comments. Instead open a TICKET here: https://www.iperiusbackup.com/contact.aspx
**********************************************************************************
PLEASE NOTE: if you need technical support or have any sales or technical question, don't use comments. Instead open a TICKET here: https://www.iperiusbackup.com/contact.aspx
*****************************************