In 2024, ransomware continues to represent one of the most significant threats to global cyber security. The threat landscape has evolved, with increasingly sophisticated and diverse cyber attacks. Cybercriminals no longer just encrypt data and demand a ransom; they use a quadruple extortion strategy that includes data encryption, data exfiltration, DDoS attacks, and direct contact with customers or partners to increase pressure on victims.
The trend is particularly concerning, as ransom demands have increased by 500% in one year, with an average of $2 million paid per attack. Even though the incidence of attacks has slightly decreased, the fact that more than half of the affected organizations have paid the ransom demonstrates the effectiveness of these criminal tactics.
Types d’Attaques d’Extorsion
To better understand the complexity and evolution of ransomware threats, let’s look at the main types of extortion attacks used by cybercriminals:
- Single Extortion: Data encryption with a ransom demand for the decryption key.
- Double Extortion: Data encryption and theft, with the threat of publication if the ransom is not paid.
- Triple Extortion: Threats extended to customers and partners, creating further pressure on the victim.
- Quadruple Extortion: Adds DDoS attacks to paralyze operations until the ransom is paid.
The Evolution of Ransomware: Quadruple Extortion
The evolution of ransomware tactics has led to the quadruple extortion strategy, which combines multiple levels of threats to maximize pressure on victims. This strategy includes:
- Data Encryption: Encrypts data and demands a ransom for the decryption key.
- Data Exfiltration: Steals data and threatens to publish it online if the ransom is not paid.
- DDoS Attacks: Launches Distributed Denial of Service (DDoS) attacks to disrupt the organization’s operations.
- Direct Contact with Customers or Partners: Threatens to contact customers, partners, or other stakeholders to create additional pressure on the victim organization.
This multi-faceted strategy makes ransomware even more dangerous and difficult to manage, increasing both risks and costs for victims.
Guidelines to Follow in Case of a Ransomware Attack
In the context of quadruple extortion ransomware attacks, it is essential to follow some guidelines to minimize damage and initiate the recovery process. Here are some key recommendations:
Immediate Actions
- Isolation: Immediately disconnect the infected device from the network.
- No Ransom Payment: Avoid paying the ransom to not fuel further attacks.
- Reporting: Inform authorities and involve cyber security specialists.
Preventive Measures
- Email Protection: Block spam and use multi-factor authentication.
- Antivirus and Antimalware: Use security solutions on all devices, including mobile.
- Firewalls and Threat Detection: Implement firewalls and threat detection systems.
- Network Segmentation: Limit the spread of ransomware by segmenting the network.
- DDoS Prevention: Adopt solutions against DDoS attacks.
Backup Policies
- Regular and Encrypted Backups: Perform regular and encrypted backups on external resources, such as the Cloud. Follow the 3-2-1 security rule, which involves keeping 3 copies of the data, on 2 different media, with at least 1 copy stored off-site (e.g., in the cloud).
- Use External Backups: Use software like Iperius Backup to perform data backup and restoration in case of an attack.
Staff Training
- Threat Awareness: Train staff to recognize attack techniques, such as ransomware that can arrive via phishing emails, compromised websites, infected software downloads, or exploit vulnerabilities in software systems.
- Response Plan: Define a response plan with clear roles for effective reaction. Ensure every team member knows exactly what to do during an incident. Regularly conduct simulations to test and improve the plan.
By following these tips, organizations can reduce risks and ensure a quick and effective recovery in case of a ransomware attack.
Protection Tools Against Attacks
To defend against quadruple extortion ransomware attacks, it is crucial to use advanced tools:
- Norton 360: Offers comprehensive protection against various types of ransomware, including quadruple extortion threats, and includes data backup features.
- Bitdefender: Known for its robust security features, it offers specific protection against ransomware and advanced solutions to prevent data exfiltration and DDoS attacks.
- Kaspersky: Besides ransomware protection, provides online security tools, password management, and advanced features for network segmentation and preventing targeted attacks on business clients and partners.
Prevention and Backup with Iperius
Prevention is key to effectively defending against ransomware attacks. Here are some practical tips on how to use Iperius Backup to protect your data and ensure a quick recovery in case of an attack.
Recommended Backup Types
- Off-Site Backup: Use online backups on Cloud and FTP, as these destinations are unreachable by ransomware.
- Removable External Media: Use USB disks and RDX cartridges. Rotate these media and store them outside the company.
Backup Strategies
- Daily Backups: Perform daily backups using Complete + Incremental or Complete + Differential modes.
- Weekly and Monthly Backups: Start with complete backups and then update only new or modified files. Use image backups for a quick clean system restore.
NAS Protection
- Avoid Network Sharing: Do not share any NAS folder on the network. Use the FTP server for backups.
- Limit Write Permissions: Grant write permissions to only one user for shared folders on the NAS.
- Install Iperius Backup as a Windows Service: Configure Iperius Backup as a Windows service to ensure automatic and continuous backups even in the absence of a logged-in user.
Intelligent Scanning
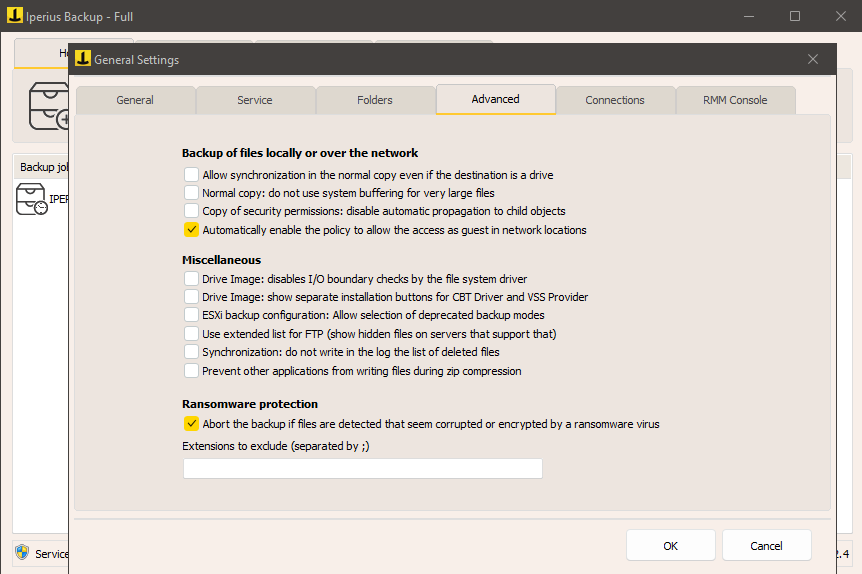
- Corrupted File Detection: Use Iperius Backup’s intelligent scanning function to detect the presence of corrupted or encrypted files by ransomware before performing the backup, thus protecting previous backups from compromised copies.
By following these tips and strategically using Iperius Backup, you can significantly enhance your protection against ransomware attacks and ensure quick and effective recovery in case of data compromise for maximum resilience.


PLEASE NOTE: if you need technical support or have any sales or technical question, don't use comments. Instead open a TICKET here: https://www.iperiusbackup.com/contact.aspx
**********************************************************************************
PLEASE NOTE: if you need technical support or have any sales or technical question, don't use comments. Instead open a TICKET here: https://www.iperiusbackup.com/contact.aspx
*****************************************