One of the biggest IT Security challenges to and risks for companies in recent years has been the proliferation of the Ransomware viruses, the most infamous of which are well known by the names Cryptolocker, Cryptowall, CTB-Locker, TeslaCrypt, Wannacry, and there are many more too.
The rapid spread of this type of virus is due to a number of simple, but key, factors that include the ability to trick users with legitimate seeming emails (containing the virus attached under the guise of an invoice or other document) and the difficulty of locating the virus in time due to the actions taken by the virus itself and the continued appearance of newer variants of the same type of virus.
But what exactly does ransomware, like Cryptolocker, do? And why have these types of virus been defined as devastating for the security and retention of business and home user data?
Well, ransomware viruses do a very simple thing and they do it well – they encrypt data. This makes the data inaccessible (usually by making the data unable to be opened, for example) and the viruses will generally target files that are most likely to be important, such as Excel files, Word documents, JPEG images (most likely all personal photographs), PDFs, Zip files, etc …
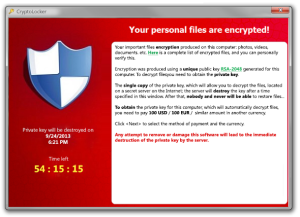
Once the files have been encrypted by the virus it will not be possible to open the files without the encryption password and without using specialist software. Once the infection of the computer or network has been completed Cryptolocker will display a screen that informs the user that all their files have been encrypted and that they will have to pay a ransom by a certain deadline in order to have access restored to their files. A screenshot of this screen is attached below:
If the infection gets to this stage then things have gotten very serious and at this point many companies have been known to simply pay the ransom to regain access to their files and data. However, before going to this extreme for a solution to this problem – which ultimately does nothing but finance unscrupulous criminals who profit from the work of honest people – the best thing to do is to rely on a company that specialises in the recovery of files or liaise with and take advice from companies that have gone through similar experiences and know how to act when presented with this situation.
Thanks to the current state of knowledge about many of the early variants of Cryptolocker and other ransomware viruses it is possible to rely on services that allow the decryption of infected devices and recovery of affected data with minimal expenditure. Doctor Web, a Russian company that develops the Dr.Web antivirus software, is one of the companies leading the fight against this type of infection whilst developing the tools to fight this problem and aid in the recovery of encrypted files. You can read further information from Doctor Web here -
http://antifraud.drweb.com/encryption_trojs/?lng=en%20.
The following are the guidelines that are to be followed when your device has been infected ransomware, such as Cryptolocker.
- If you find that some files have become inaccessible, but you have not yet received the ransom request window, the advice is to immediately turn off the computer, unplug it from the mains and disconnect any external disk or other data storage device to prevent further damage and infection. Take the device to a professional for a full system cleaning before attempting to restart the device.
- If the infection has already been completed and the ransom request window has been displayed the advice is to take note of the links provided by the virus to pay the ransom (to be used as a last resort) and then proceed with the virus removal. All network devices, external disks and any other disks should be unlinked from the device to prevent further spreading of the virus and the device should also be removed from the network to ensure that other machines are not also infected. In this case we will use a USB flash drive to copy all removal, cleaning and data recovery tools and to complete the virus removal.
- At this stage we proceed with the removal of the virus and we attempt to recover the files. For this we rely on the aforementioned Dr. Web or other more famous anti-virus software such as Kaspersky and Norton/Symantec.
Here are the links from the Kaspersky website that can be used for removing ransonware viruses and attempted recovery of corrupted data:
http://support.kaspersky.com/viruses/disinfection/8005
https://noransom.kaspersky.com/
Additional scanning and removal can then be carried out with Norton Power Eraser:
https://security.symantec.com/nbrt/npe.aspx
Following this, we advise that, as soon as possible after the removal of the virus, a more “aggresive” monitoring system for possible malicious activity such as those typical of ransomware is installed on the device to prevent re-infection.
The most often recommended version of this software is HitmanPro.Alert:
http://www.surfright.nl/en/cryptoguard
So far we have talked about the worst case scenarios that can arise, namely that all of our files are “temporarily” lost and we have no backup of this data. This puts us in the position of having to entrust data recovery experts or that we have to personally use special instruments for removing ransomware viruses, such as Cryptolocker, and decrypting files. Finally, if all of this does not work, you would, as a last resort, have to pay the ransom and hope that the hackers who packaged the virus can still be reached and they have not been arrested or moved onto other criminal ventures (in which case you should inquire about recent police operations that may in some way have had access to the source of the virus and then the keys for decryption).
In this article we also wish to talk about prevention of ransomware attacks and the ways that to protect yourself from Cryptolocker and all other ransomware viruses so that any attacks cannot affect your company and see you lose all of your personal data.
The basic guidelines to follow are, of course, the installation of an antivirus software and/or a firewall, and, as the Wannacry case has taught us, always keep your operating system up to date with the latest patches provided by Microsoft. In addition to this, the best way to emerge unscathed from a ransomware virus attack is to have an accurate and effective data backup strategy. In this second part of the article we will provide some tips on the best way to make a backup of your data using the Iperius backup system. The best way we have found to explain this process is through the following set of questions and answers.
- What backup types are recommended in order to recover files after a cryptolocker attack?
- First of all, we advise that any backup used are offsite or online via the Cloud or FTP as these locations cannot be reached by the virus. These backups are stored on removable external media such as USB drives and RDX cartridges and these can be replaced in rotation on a monthly basis and can be stored off-site by the company, making it useful in the event of theft or environmental disasters. We choose two or more destinations for our backup with different operations and schedules to ensure complete backup coverage. Iperius can perform online backups to Google Drive, Dropbox, OneDrive, Amazon S3, Azure and any FTP server.
See the following tutorial:
https://www.iperiusbackup.net/en/iperius-backup-3-8-cloud-backup-and-online-storage/
https://www.iperiusbackup.net/en/make-incremental-ftp-backup-iperius-online-storage/
https://www.iperiusbackup.net/en/make-incremental-ftp-backup-upload-iperius/
- How often should I schedule the backup?
- The key recommendation is to create different backup operations, with different schedules. There must be a daily backup, but also backups run weekly and monthly. This is prevent the previous backups being inadvertently overwritten with encrypted copies of the files in the case of a ransonware attack (so to have a margin of time to notice and deal with the infection).
See the following tutorial:
https://www.iperiusbackup.net/en/how-to-schedule-automatic-backup-with-iperius/
- What backup mode should I use?
- The advice is to make daily backups with full mode + Incremental or Full + Differential (to have a history of changed files), and on a weekly and monthly backups that initially do a full backup and then update this backup only new or changed files. This type of backup can be done on FTP / SFTP destinations, external drives, RDX, NAS, server, or computer network.
Finally, it is highly recommended you perform a backup image (drive image), or a full backup of the entire disk weekly or monthly basis, because it allows us to recover and clean the whole system in a short time, and because the backup image, being a large file, is not affected by the virus.
See the following tutorial:
https://www.iperiusbackup.net/en/backup-types-with-iperius-full-incremental-differential/
https://www.iperiusbackup.net/en/system-image-backup-drive-image-with-iperius/
- I know that the virus can also reach the network folders. How do I protect my NAS and where do I back up?
- This question is very important one. There are several ways to protect a NAS from the entrance of a ransomware virus as Cryptolocker. You can, for instance, choose not to share any of the NAS network folders, and instead use its FTP server. With Iperius you can configure an FTP type on the NAS backup. In this way, the NAS will not be any way accessible to the virus.
Or, should you wish to keep the network shares of the NAS accessible, you must ensure that only a single user has write access to the folders. You can then create a specific account for backing up Windows or Active Directory for computers that are in a domain, then use this account to run the Iperius service (or for “impersonation”of Iperius process), to deal with running the scheduled backups. In this way, only Iperius will have write access to the NAS folders (where of course only to that user will have given write access to shared folders).
See the following tutorial:
https://www.iperiusbackup.net/en/installation-windows-service-iperius-backup/
https://www.iperiusbackup.net/en/backup-nas-make-iperius/
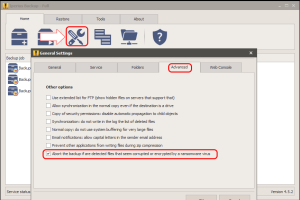
A new option to protect your backup from Cryptolocker
Finally, as of version 4.5.2 of Iperius, a new and important option was introduced which detects the presence of corrupt files or encrypted by ransomware virus before doing the backup. This intelligent file scanning protects older backups from being overwritten by copies of the compromised files, and then preserves them from virus attack. In the image below we see how to enable this option:
Some more information about ransomware:
https://www.microsoft.com/security/portal/mmpc/shared/ransomware.aspx

I have install Iperius Backup and I want to backup exchange mailbox server 2016, I have added role and permission according mention tutorials in this site to the user, to access the mailbox.
it not connect to server. display error:
—————————
Test gave negative result: Connecting to remote server Ser03.mail.com failed with the following error message : Access is denied. For more information, see the about_Remote_Troubleshooting Help topic. (at System.Management.Automation.Runspaces.AsyncResult.EndInvoke())
—————————
Please help me
Hi,
for technical support, please open a ticket on https://support.iperius.net.